Malware Using Google MultiLogin Exploit to Maintain Access Despite Password Reset
Malware that steals information is presently using MultiLogin, an undocumented Google OAuth API, to take over stoner sessions and entitlement patient access to Google services indeed after a word reset.
As per CloudSEK, the crucial vulnerability enables threat actors to sustain access to a legitimate session in an unauthorized way by facilitating cookie formation and session persistence.
On October 20, 2023, a threat actor going by the handle PRISMA initially disclosed the method on their Telegram channel. Since then, it has been included to a number of malware-as-a-service (MaaS) stealer families, including RisePro, Lumma, Rhadamanthys, Stealc, Meduza, and WhiteSnake.
When users sign in to their accounts in the Chrome web browser, the MultiLogin authentication endpoint is primarily intended to synchronize Google accounts across services (i.e., profiles).
Security researcher Pavan Karthick M stated that the method targets the "Chrome's token_service table of WebData to extract tokens and account IDs of chrome profiles logged in," as shown by a reverse engineering of the Lumma Stealer code. "This table contains two crucial columns: service (GAIA ID) and encrypted_token."
The MultiLogin endpoint is then used in conjunction with this token:GAIA ID pair to generate new Google authentication cookies.
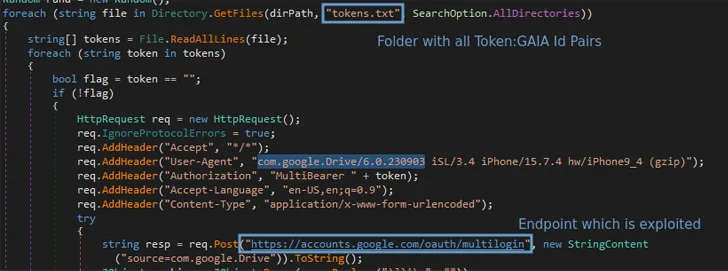
Karthick told The Hacker News that three different token-cookie generation scenarios were tested -
- When the user is logged in with the browser, in which case the token can be used any number of times.
- When the user changes the password but lets Google remain signed in, in which case the token can only be used once as the token was already used once to let the user remain signed in.
- If the user signs out of the browser, then the token will be revoked and deleted from the browser's local storage, which will be regenerated upon logging in again.
Google confirmed the attack method's existence when contacted for comment, but pointed out that users could undo the stolen sessions by exiting the affected browser.
Google informed The Hacker News that it was "aware of recent reports of a malware family stealing session tokens." "Virus attacks that steal cookies and tokens are not new; we regularly update our defenses to thwart these attempts and to protect users who are infected with malware. Google has acted in this case to safeguard any compromised accounts that have been found."
"However, it's important to note a misconception in reports that suggests stolen tokens and cookies cannot be revoked by the user," it continued. This is untrue because it is possible to remotely revoke stolen sessions using the user's device page or by simply signing out of the compromised browser. We'll keep an eye on things and make updates when necessary."
Additionally, the company advised users to enable Chrome's Enhanced Safe Browsing feature to guard against virus downloads and phishing scams.
"It's advised to change passwords so the threat actors wouldn't utilize password reset auth flows to restore passwords," Karthick stated. "Also, users should be advised to monitor their account activity for suspicious sessions which are from IPs and locations which they don't recognize."
The chief technical officer and co-founder of Hudson Rock, Alon Gal, previously revealed the specifics of the vulnerability late last year. "Google's clarification is an important aspect of user security," Gal stated.
"On the other hand, the event highlights a complex exploit that could undermine the established procedures for account security. Google's efforts are commendable, but this case emphasizes the need for more sophisticated security measures to combat growing cyberthreats, such infostealers, which are very common among hackers these days."
(After publishing, the article was revised to include more remarks from Alon Gal and CloudSEK.)





Comments